If you are searching about How to Prevent and Detect Insider Threat - Adamo Security you've came to the right page. We have 9 Images about How to Prevent and Detect Insider Threat - Adamo Security like Announcing Insider Threat Program Evaluator Training from the CERT, How to Prevent and Detect Insider Threat - Adamo Security and also Insider Threat Program A Complete Guide - 2020 Edition ebook by. Here you go:
How To Prevent And Detect Insider Threat - Adamo Security

threat detect
10 Tips To Strengthen Your Insider Threat Program – Data, Intent And

threat intent strengthen context
Announcing Insider Threat Program Evaluator Training From The CERT
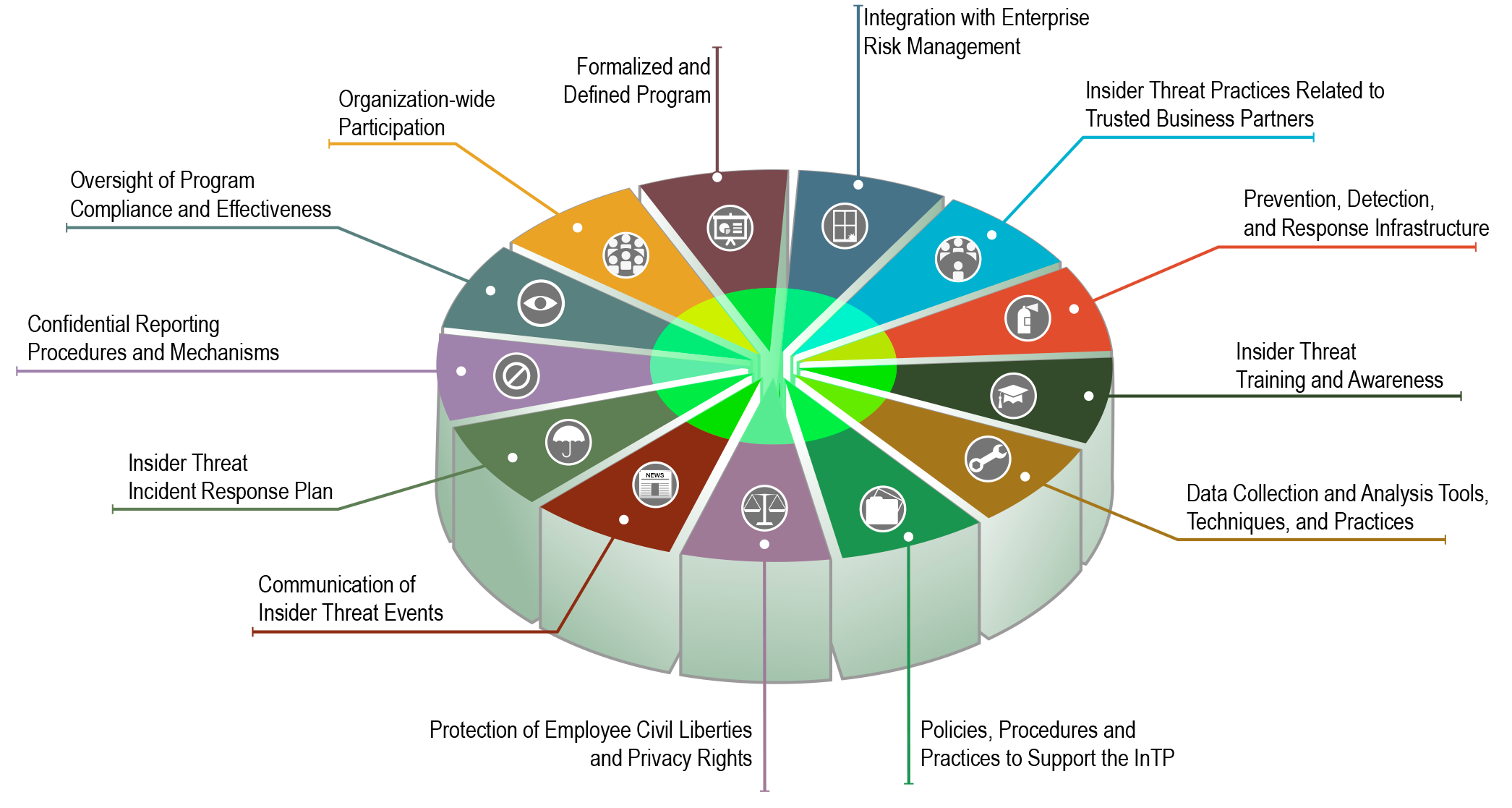
threat program cert evaluator announcing components
IIA Issues Guide On Auditing Insider Threat Programs | Internal Audit 360

iia auditing
Why Is The Success Of The Insider Threat Program - AlejandrogroAvery

Insider Threat Program A Complete Guide - 2020 Edition Ebook By

20 Must-Read Insider Threat Blogs For 2020

threat insider lookout dasera
Insider Threat - Unleashed Gives You The 10 Reason That Insider Threat

insider threat threats graph business practices mitigating produced following shows report real
Maturing Your Insider Threat Program Into An Insider Risk Management

insider threat program management risk sei goal real model
Iia issues guide on auditing insider threat programs. Threat intent strengthen context. How to prevent and detect insider threat
0 comments
Post a Comment